Tor anonymity infiltrated: Law enforcement monitors servers successfully
Tor is an important service on the Internet when it comes to anonymity. It is free and can be used by anyone to hide information such as a device's public IP address.
Tor is used by people from all over the world to overcome censorship. While it is used for good, it is abused as well. Cybercriminals are using Tor for the very same purpose: to stay anonymous and evade law enforcement.
Also of interest: Tor launched WebTunnel Bridge recently as a new way to overcome censorship
Anonymity cracks
Law enforcement agencies in Germany have monitored Tor servers for months to identify individual users. The agencies managed to identify a server of the ransomware group Vanir Locker that the group operated from within the Tor network.
The group announced that it would release copied data from one of its latest coups on the server. Law enforcement agents managed to identify the location of the server by using a technique that is called Timing Analysis.
Timing Analysis is used to link connections to nodes in the Tor network to local Internet connections. The method depends on the monitoring of as many Tor nodes as possible, as this increases the chance of identification.
This confirms that law enforcement is monitoring Tor nodes. It seems likely that German law enforcement agencies are not the only ones using the technique for identification.
A state office of criminal investigations took over the Tor address of the ransomware group and redirected it to a new page. This prevented the release of the stolen data on the page.
Reporters from ARD, a publicly financed broadcasters, were able to view documents that confirmed four successful identifications in a single investigation, according to reports. Agencies used the technique to identify members of a child abuse platform.
Closing Words
It is not only law enforcement agencies that may use the technique to identify criminals. Oppressive regimes may use the very same method to identify users who try to stay anonymous to evade prosecution.
A blog post on the Tor Project blog sheds some light on the issue. It addresses the identification in the child abuse case. The maintainers admit that they did not have access to sources, but believe that Tor continues to be one of the best options to stay anonymous for the majority of Internet users.
They would like to receive access to the information to find out if there is an issue with the service that may be fixed.
What is your take on this? Do you use Tor at all? Feel free to write a comment down below.
RECOMMENDED NEWS

How to enable Tab Previews in Firefox
Mozilla released Firefox 123 a few days ago, and it comes with a new feature. The browser now suppo...
The Windows Windows App is real - replacing Remote Desktop app
Microsoft is once again shifting things around and making things confusing for users of its product...

Avast Free Antivirus: Security Starts with Good Practices
Cybersecurity has become a priority for users of all levels. With the growing number of attacks and...
What you need to know about DeepSeek AI
Companies and organizations like Nvidia, OpenAI, Microsoft, Meta, Google, or Anthropic have dominat...
Cybersecurity Experts Warn of Privacy Risks in Modern Automobiles
A pair of hackers, Sam Curry and Shubham Shah, have exposed alarming security vulnerabilities withi...
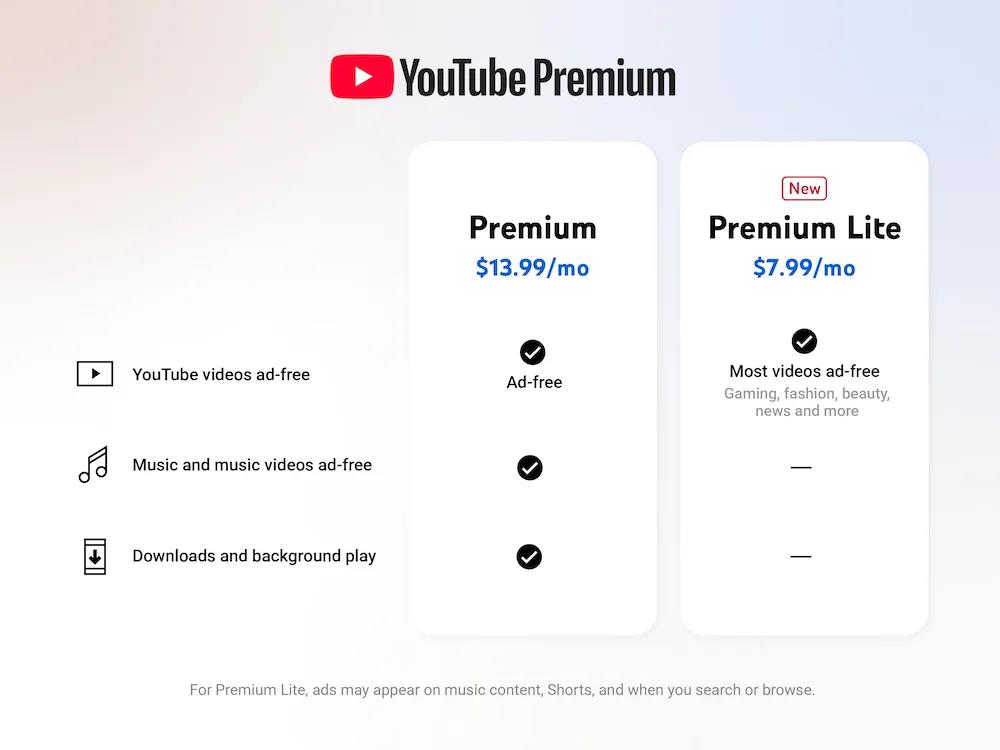
YouTube Premium Lite Launches in the US for $7.99 a Month
As expected, YouTube has officially launched its Premium Lite subscription in the United States for...
Comments on "Tor anonymity infiltrated: Law enforcement monitors servers successfully" :