Microsoft Edge fixes 0-day vulnerability: confirms all Chromium-based browsers vulnerable
Microsoft released a security update for its Edge web browser that address several security issues, including one that is exploited in the wild.
Google released security updates for its Chrome web browser on March 26, 2024. The official release announcement on the Chrome Releases Blog did not reveal that Google was aware that one of the issues was exploited in the wild.
The critical security issue CVE-2024-2883 -- Use after free in ANGLE -- was fixed in Chrome Stable and Chrome Extended Stable on March 26, 2024.
Microsoft pulled an earlier release of Microsoft Edge 123. The company has now released 123.0.2420.65, which addresses eight unique security issues in the browser.
One of them is CVE-2024-2883, which affects all Chromium-based browsers. The official CVE page on Microsoft's website reveals that the issue is already attacked in the wild.
Microsoft writes: "Google is aware that an exploit for CVE-2024-2883 exists in the wild."
The Microsoft Edge release notes page confirms this as well: "This update to Stable channel contains a fix for CVE-2024-2883, which has been reported by the Chromium team as having an exploit in the wild."
This confirms that all Chromium-based browsers, including Google Chrome, are affected by the issue. ANGLE or the ANGLE Project, stands for Almost Native Graphics Layer Engine.
Google announced ANGLE in 2010 and described its goal in the following way: "The goal of ANGLE is to layer WebGL's subset of the OpenGL ES 2.0 API over DirectX 9.0c API calls. [..] it will enable browsers like Google Chrome to run WebGL content on Windows computers without having to rely on OpenGL drivers."
Update immediately
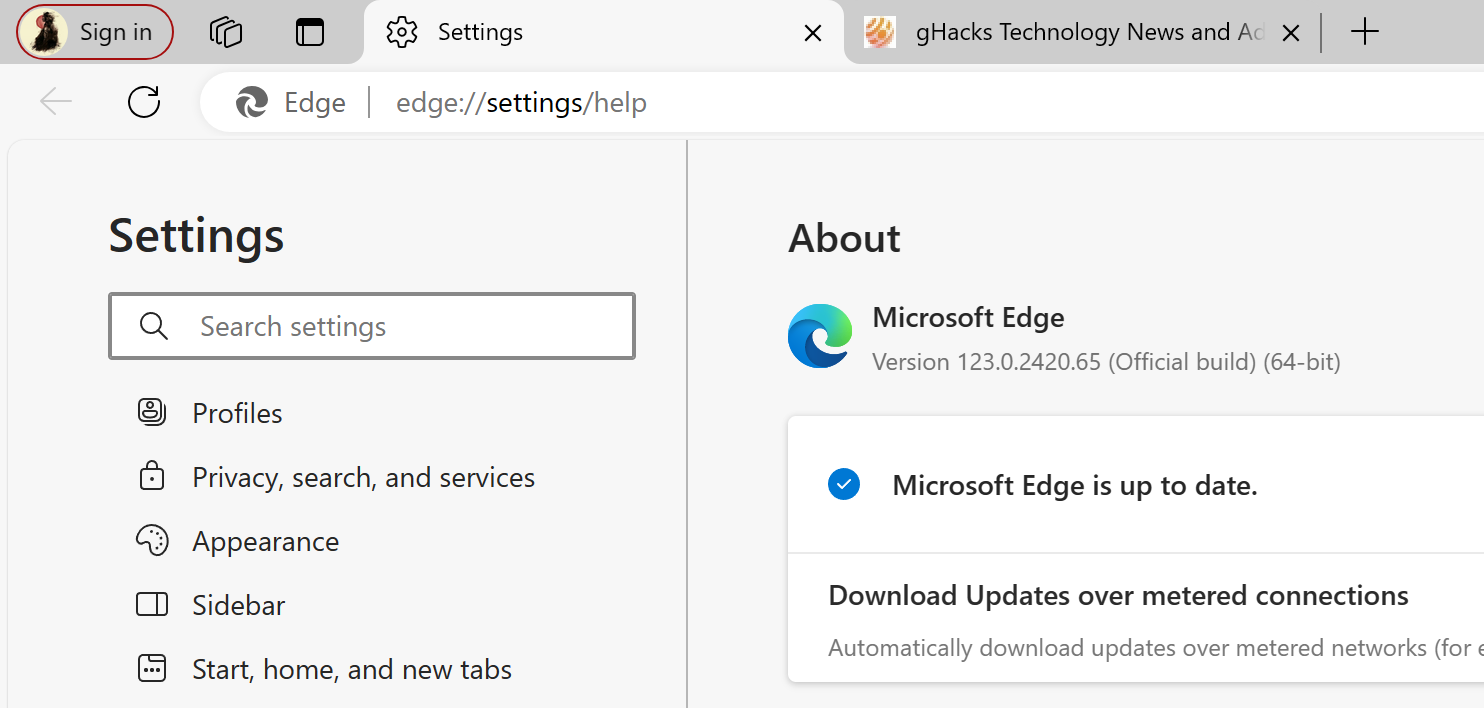
Chromium-based browser users may want to update the browser immediately, provided that an update is available.
Most may load chrome://settings/help in the browser's address bar to open the about page. The "chrome" protocol is usually redirected to the browser's specific protocol. This is edge:// for Microsoft Edge, or vivaldi:// for Vivaldi.
It lists the current version that is installed on the system. The browser checks for updates when the page is opened. Any update that is found is downloaded and installed at this point. Note that you need to restart the browser to complete the installation of the update.
Microsoft Edge should list version 123.0.2420.65 after installation of the update.
Load the page in any Chromium-based browser installed to make sure that it is up to date. Not all browser makers may push out updates immediately. If that is the case, check back at a later point in time.
Closing Words
Mozilla patched two 0-day vulnerabilities in its Firefox web browser as well this week. The patch was released days after the release of Firefox 124.0.
It is important to keep an eye on browser updates that companies release. This allows you to react quickly to major issues that could potentially put your data and systems at risk.
Now You: when do you update your browsers?
RECOMMENDED NEWS

iOS 17.1.2, iPadOS 17.1.2 and macOS 14.1.2 patch 2 actively exploited security vulnerabilities
Apple has released a point update for iPhones, iPads and Macs. iOS 17.1.2, iPadOS 17.1.2 and macOS ...

Steam Game Recording Beta announced: a built-in tool to record your gameplay videos
Steam has announced a new feature in its desktop client, called Game Recording. This built-in video...
Windows 10 Support until 2030? 0Patch makes it possible
Micro-patching service 0Patch will support Microsoft's Windows 10 operating system until 2030. ...

New Excel Copilot Feature: Access Data from Word, PowerPoint, and PDFs
Microsoft has announced a significant enhancement to its Copilot feature in Excel, enabling users t...

Windows bug blocks BIOS updates for Lenovo ThinkPad laptops
Lenovo ThinkPad owners are facing a headache with BIOS updates due to a recent change made by Micro...

Google One may soon let you backup and restore your eSIM data
Google is reportedly developing a feature to enhance the backup process for Android devices. It may...
Comments on "Microsoft Edge fixes 0-day vulnerability: confirms all Chromium-based browsers vulnerable" :