LogoFail vulnerability affects many Windows and Linux devices
Many commercial computers are vulnerable to a set of vulnerabilities that exploit flaws in the processing of startup logos during boot.
Security researchers at Binarly have disclosed security vulnerabilities in system firmware used by computer manufacturers during the boot process. The vulnerability impacts x86 and ARM-based devices.
The set of vulnerabilities is found in BIOS software created by different companies, including the three largest independent bios vendors AMI, Insyde and Phoenix. These are widely used in the industry, for instance in computers by Intel, Acer or Lenovo. Alex Matrosov, CEO at Binarly, says that about 95% of all computers use firmware from the three bios vendors.
Binarly says that it estimates that almost any device produced by these vendors is vulnerable "in one way or another".
In simple terms, LogoFail exploits vulnerabilities in image parsers that affected devices use to display vendor logos during boot. Different image parsers are used to display different image types, and "they are rife with vulnerabilities" according to Matrosov.
A hacker needs to replace the vendor image with a specially prepared one to exploit the vulnerability and execute arbitrary code on the machine. Binarly explains that attackers may store malicious logo images on the EFI System Partition or inside unsigned sections of a firmware update. The images are then parsed during boot and this initiates the attack on the device.
The attack allows attackers to bypass security features such as Secure Boot. Binarly notes that this also affects hardware-based Verified Boot systems, including Intel Boot Guard, AMD Hardware-Validated Boot and ARM TrustZone-based Secure Boot.
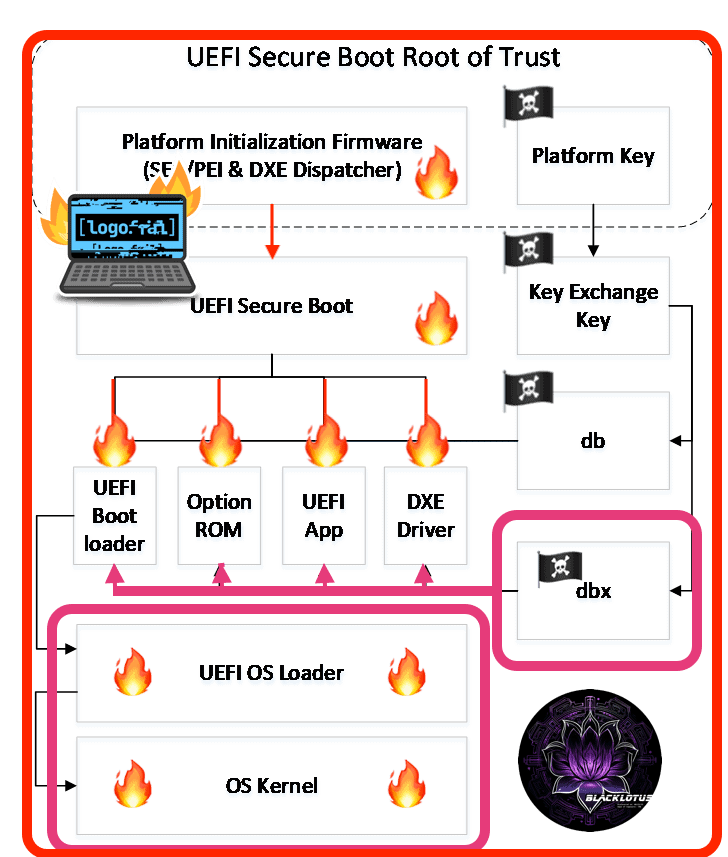
Binarly believes that the attacker may be able to bypass "most endpoint security solutions" and integrate a persistent stealth firmware bootkit on the system. In other words, attackers may exploit LogoFail to compromise the security of many computer systems.
Attacks and protection
Attackers need to gain administrative access on target devices to exploit the vulnerability. This can be achieved through malicious payloads planted on the system, for instance by getting the user to run malicious software, or through exploits.
Once access is gained, the attacker would replace the vendors boot logo with a malicious logo, which the device would then load during boot.
An attacker would be able to disable UEFI security features, such as SecureBoot, modify the boot order and execute malicious software to infect operating systems.
Firmware updates are available or will be released for some of the affected devices. Administrators may want to check for firmware updates for devices that they manage that address the vulnerabilities. Not all devices will receive firmware updates, however. Especially devices that are no longer in support may not receive them.
A search for "device name firmware update" or "device name drivers" should return the driver download website of the manufacturer of the device.
Users on devices without firmware updates need to be extra cautious and use protections to avoid the initial attack on the device (which needs administrative access).
Additional information about the vulnerability is found on the Binarly website and on the CERT database.
RECOMMENDED NEWS
PSA: Raivo OTP for iOS was acquired by Mobime a few months ago
Raivo OTP, a popular authenticator app for iOS, has been acquired by a company called Mobime. The a...

Apple releases iOS 18.1, macOS 15.1 and iPadOS 18.1 with Apple Intelligence
Apple has released iOS 18.1, macOS 15.1 and iPadOS 18.1 updates just a month after the release of i...
Steam Now Warns Buyers About Abandoned Early Access Games
Valve has introduced a new warning system on Steam to alert buyers when an early access game appear...
Could Amazon's 'Buy for Me' redefine the future of online shopping?
Amazon is taking artificial intelligence to the next-level with its newly announced “Buy for me” fe...
Nintendo delays Switch 2 pre-orders in the U.S. due to tariff concerns
Nintendo has announced a delay in the pre-orders for the Switch 2. The company cited "the potential...

ChatGPT Deep Research is now available for free users, with some limitations
OpenAI has announced that its research tool, Deep Research, is now available for free ChatGPT users...
Comments on "LogoFail vulnerability affects many Windows and Linux devices" :