Security experts have discovered new Intel Spectre vulnerabilities
Researchers from ETH Zurich have uncovered a new class of vulnerabilities linked to Intel processors. They were able to bypass Intel's defenses against Spectre.
Spectre is a class of vulnerabilities that was originally identified in 2018, along with Meltdown, a similar exploit that affected AMD chips. These flaws exploited speculative execution, which in turn leaked data. Though the vulnerabilities were patched 7 years ago, Microsoft released a Registry security mitigation a year ago to protect against the vulnerability.
As it turns out, Spectre has resurfaced in a new persona. The researchers from ETH Zurich have labeled the data-leaking flaws as Branch Prediction Race Conditions (BPRC). These vulnerabilities primarily affect Intel CPUs from the 9th generation (Coffee Lake Refresh) down to the 7th generation (Kaby Lake).
The researches said that the branch predictors on Intel processors are updated asynchronously inside the processor pipeline, as a result of which there are potential race conditions. In such a scenario, two or more processes or threads could attempt to access and update the same information concurrently, and this could lead to chaos. They discovered an exploit was possible where a processor switches privilege levels, such as from user to kernel, while branch predictor updates are still in flight. This can lead to a new attack vector, Spectre v2, which allows unauthorized code injection thanks to elevated privileges. The security experts call it Branch Privilege Injection (BPI). These issues affect all sorts of computers, from PCs to servers in data centres.
Here is how the issue was described: “We can use the vulnerability to read the entire contents of the processor’s buffer memory (cache) and the working memory (RAM) of another user of the same CPU.”
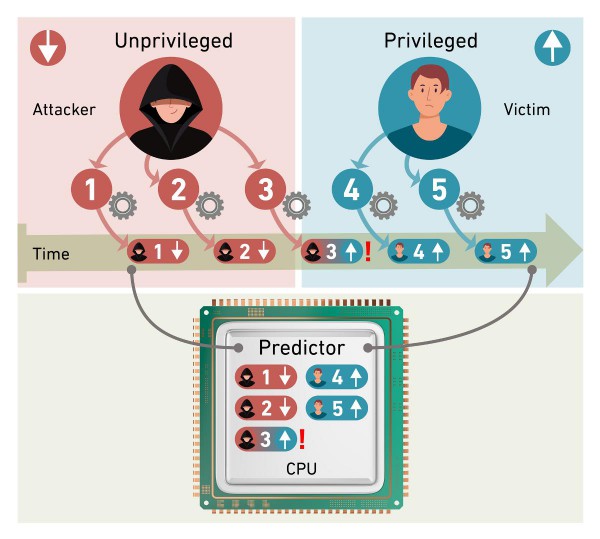
The discovery by the Swiss team indicates that there is a performance impact, up to 2.7 percent overhead for the microcode mitigation on Alder Lake, though Intel is yet to comment on this issue.
Intel has released a microcode update to address the new flaw, which has been designated as CVE-2024-45332. The Indirect Branch Predictor Advisory describes the issue as follows: Potential security vulnerabilities in some Intel® Processor indirect branch predictors may allow information disclosure. Intel is releasing microcode updates to mitigate these potential vulnerabilities.
It is worth noting that products from AMD and ARM don't appear to be affected by this new exploit.
Source: The Register, ETH Zurich
RECOMMENDED NEWS

If your Windows PC freezes, Avira security software may be the culprit
A recent update for Avira antivirus software for Windows seems to have a negative impact on system ...

The most popular passwords of 2023 are easy to guess and crack
Each year, analysts at various Internet security companies release lists of the most used (and know...

Windows 11 version 24H2 may block devices without SSE 4.2 support
Recent Windows 11 development builds include new hardware compatibility rules that block the operat...

Windows 11 set up is automatically enabling OneDrive folder back up for users
Microsoft has made yet another silent change to the way the initial setup of Windows 11 works. The ...

Microsoft increases prices for Xbox consoles, accessories and new game releases
Microsoft has announced a significant price increase for its Xbox consoles and accessories effectiv...
Epic Games says Apple has blocked its Fortnite submission in the U.S. and EU App Stores
A week ago, Epic Games was celebrating its impending return to iOS. But now, it has announced that ...
Comments on "Security experts have discovered new Intel Spectre vulnerabilities" :